Complete Admin UI Management for Identity Claims and Roles

The latest ServiceStack v8.7 Release completes our transition to ASP .NET Core Identity Auth with management APIs and Admin UIs for managing Identity Auth Roles and Claims for both Users and Roles.
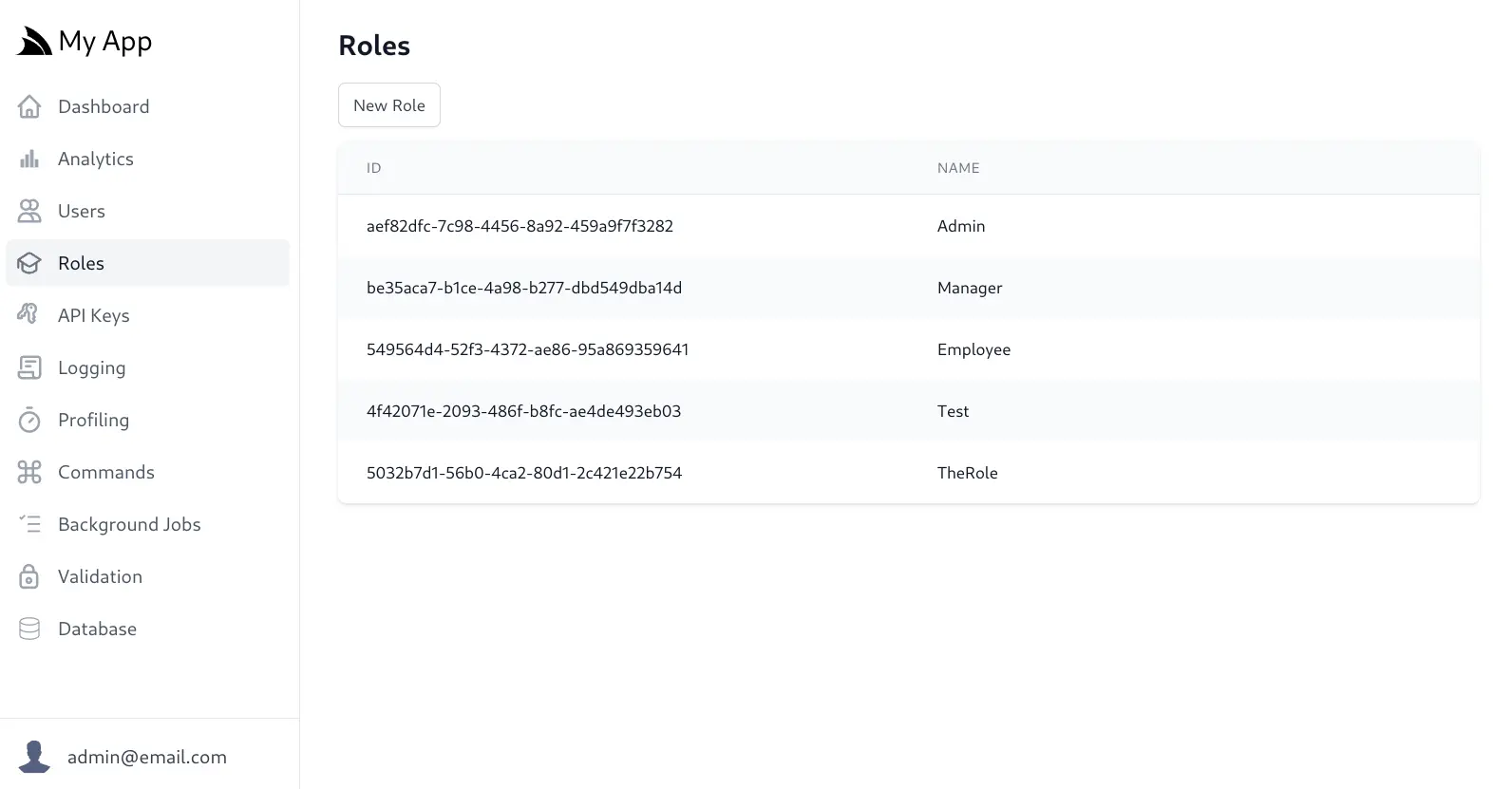
All ServiceStack Apps now includes a complete IdentityAuth Management Admin UI which can Add/Remove Roles from the new Identity Roles Admin UI:
Custom Application Roles
If your App uses an extended IdentityRole data model, it can be configured with:
services.AddPlugin(
new AuthFeature(IdentityAuth.For<ApplicationUser,ApplicationRole>(...)));
If it's also configured to use a different PrimaryKey type, it can be configured with:
services.AddPlugin(
new AuthFeature(IdentityAuth.For<AppUser,AppRole,int>(...)));
IdentityAuth Role Claims
The Edit Role Admin UI can also be configured to Add/Remove Claims to a Role, e.g:
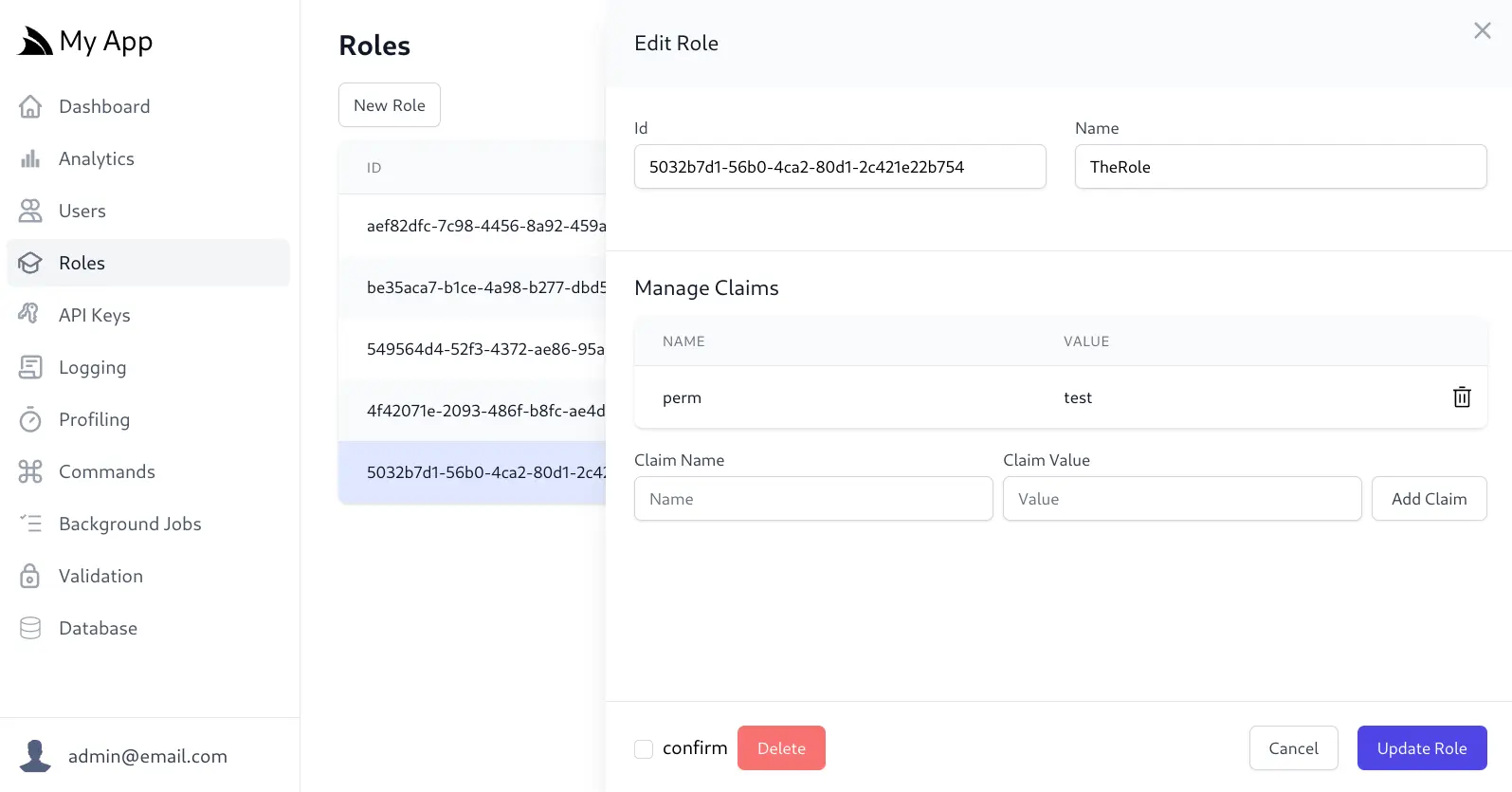
Any Added or Removed Claims are only applied after clicking Update Role, likewise you can exit the UI without applying any changes by clicking Cancel.
Claims added to Roles have similar behavior to having Claims individually applied to all Users with that Role such that when a User is Authenticated they're populated with all claims assigned to their Roles in addition to their individual User Claims.
IdentityAuth User Claims
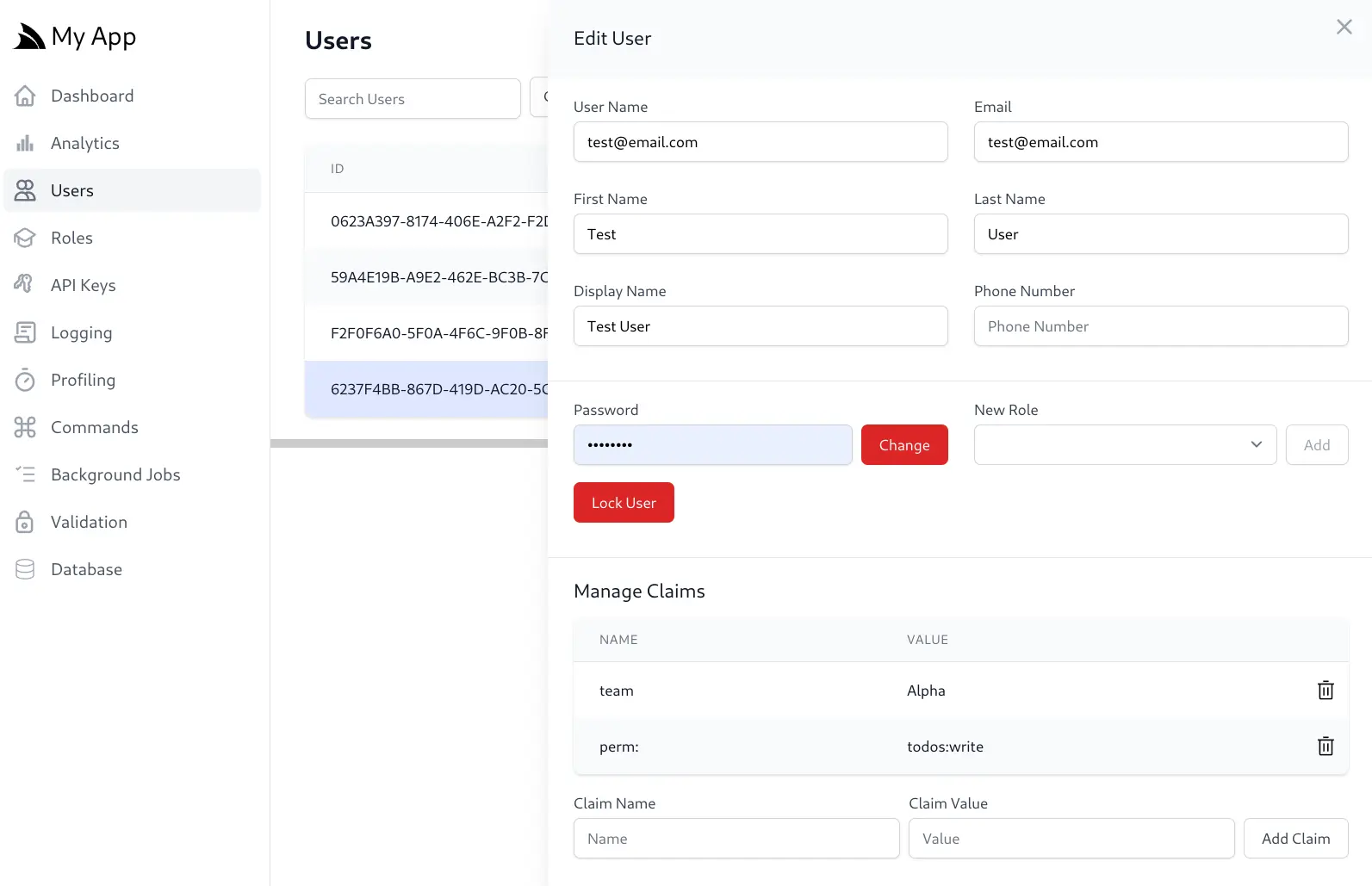
Whilst the new User Claim Management UI allows you to assign Claims to individual Users:
Validating Claims
Claims are attestations or attributes about a User which we can use to restrict access to APIs to only Users who
have been assigned that claim. We could use this to implement a permission system that restricts usage with a
todos:write permission with something like:
[ValidateHasClaim("perm", "todos:write")]
class CreateTodo {}
Normally this would result in the generic missing claims error message:
But as the perm claim has a customized error message:
HasClaimValidator.ClaimErrorMessages["perm"]= "`${Value} Permission Required`";
It will generate that Error Response instead:
Which is a good example showing how HasClaimValidator.ClaimErrorMessages can be used to add custom error messages
for your own custom claim validation.
Inspecting Claims inside Services
You can also inspect and validate a Users Claim by inspecting the Authenticated ClaimsPrincipal, e.g:
public class TodoServices : Service
{
public object Any(CreateTodo request)
{
var user = Request.GetClaimsPrincipal();
if (!user.HasClaim("perm", "todos:write"))
throw HttpError.Forbidden("todos:write Permission Required");
var allUserClaims = user.Claims.ToList();
//...
}
}